Business Continuity and Incident Response both fall under the Information Security Program umbrella, designed to complement each other to protect the Confidentiality, Integrity, and Availability of data and information technology assets. Both follow a similar set of steps in the development and execution of documented strategies. Incident Response is typically used to plan for scenarios that include the potential for exposure of sensitive data, or unauthorized access of IT. Most of these threats are associated with cybersecurity risk.
The Business Continuity Team at CU*Answers oversees the Incident Response program for the CUSO, working closely with Networking and Security Operations as well as Internal Auditing for compliance purposes. Multiple audits and examinations are conducted on a regular basis, internal and independent, with reporting provided to Senior Management and the Board of Directors. Results of these audits and examinations are reviewed as part of our SSAE-18 audit process with both SOC I and SOC II reports available at https://www.cuanswers.com/about/due-diligence-materials/.
A key component of the Information Security Program
Incident Response is a critical component of the Information Security Program, identifying processes and procedures to follow in the event of a security attack. While controls are implemented to prevent, deter, and detect attacks, bad actors are often skillful in finding their way around (or sometimes even through) these controls, or are able to identify and exploit a vulnerability before teams have had a chance to remediate it.
Incident Response requires a set of skills and experiences not often found within the employee base of most financial institutions. It is the next evolution of cybersecurity awareness training, with roles and responsibilities identified for members of the Incident Response Teams. As a CUSO and core processor, CU*Answers provides regular educational webinars on the topic as well as resources and services to help credit unions address any gaps on their response teams.
The threat landscape in the cybersecurity realm is always changing as bad actors seek new methods of monetizing their efforts. It’s imperative that CUSOs and credit unions include Incident Response development as part of their overall program, seeking to continuously strengthen the security posture.
Resources available to enhance the security posture for CUSOs and credit unions.
Your Incident Response Strategy
Effective Incident Response begins with a solid risk-based Information Security Management program. As a financial institution, regular Risk Assessments should be performed to measure inherent and residual risks, uncovering areas where controls are missing or weak (relative to your risk appetite), as well as identifying likely scenarios to plan your response efforts. Along with the regular Risk Assessments, networks and systems must both be scanned for vulnerabilities, and their controls tested regularly for effectiveness.
A culture of security is perhaps the organization’s best defense against an attack. Influencing staff behavior begins with carefully designed and clearly understood security policies. An ongoing cybersecurity awareness training program is vital, given that more than 90% of all data breaches begin with social engineering tactics, such as phishing or credential theft. For those staff with specific roles on the Incident Response Team, adequate training is required to develop the skills and experience needed, as well as identifying areas where gaps exist, indicating the need for additional training or outsourcing.
Specific processes and procedures for responding to security incidents must be documented and validated through an ongoing testing program. These must address each stage of an incident response, from detection and containment to remediation and recovery. Several resources are available from regulatory agencies, as well as case studies from actual incidents. These resources help to define guidelines and best practices as part of intelligence sharing activities.
Effective communication and notification during an incident response is a key element and a regulatory requirement under specific circumstances. Communications among response team members during the initial stages of an attack help to initiate proper containment strategies. Communicating with all key stakeholders is important to maintaining control of the message and protecting the reputation of the organization.
The Incident Response Team
The Incident Response Team is made up of a cross-enterprise group, responsible for quickly identifying threats to the organization, assessing the level of risk, and taking immediate steps to mitigate impact and loss. The team notifies appropriate authorities and mobilizes response and recovery teams to bring operations back to normal.
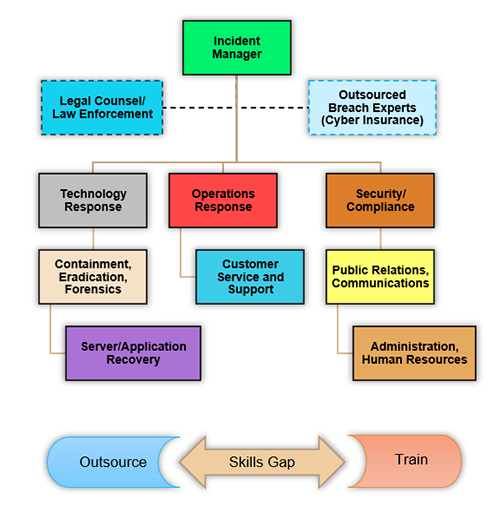
Identify and seek to fill the skills gaps of your response team members.
The Incident Response Team is comprised of a blend of internal and external parties, including legal counsel, law enforcement, cybersecurity insurance agents, as well as breach experts. Roles are often grouped by function, including the technology response, operations response to maintain at least a minimal level of services for members, as well as back-office administration. It’s important to identify the members of your Incident Response Team and seek to fill any skills and experience gaps through additional training and/or outsourcing to a trusted vendor.
Stages of an Incident Response
Whether we like it or not, every organization is either undergoing a cybersecurity attack, just coming out of a cybersecurity attack, or preparing for the next attack to begin. With a continuously evolving threat landscape, it is imperative that CUSOs and credit unions adapt to maintain a strong security posture. Recognizing that an attack is underway requires having a general knowledge of the typical stages of an Incident Response.
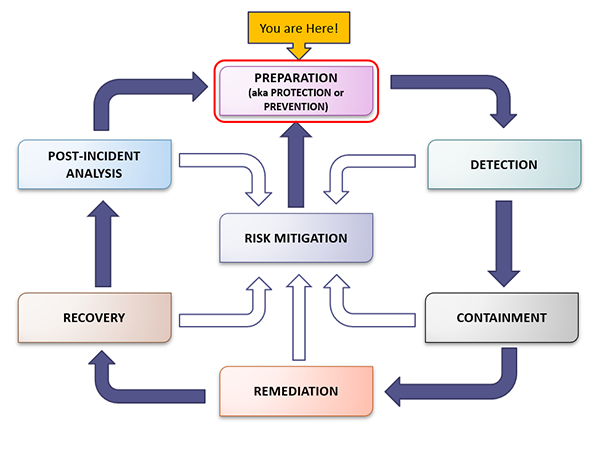
Stages of a Cybersecurity Incident
- Preparation: Like good physical health, these are the activities we do (or don’t do) to maintain a strong security posture.
- This starts with strong security policies, an ongoing cybersecurity awareness and training program, a layered approach to security controls such as multi-factor authentication, vulnerability scanning and patch management, comprehensive risk assessments, and regular testing and exercises.
- Detection: What activity on your network should you be monitoring? Where are the early signs of an attack likely to surface?
- A few key questions to ask include:
- What activity on your network should you be monitoring?
- Where are the early signs of an attack likely to surface?
- A few key questions to ask include:
- Containment: What tools and procedures will your response team follow to quickly isolate and contain the attack, whether malicious software, an exploited vulnerability, or stolen network account?
- What tools and procedures will your response team follow to quickly isolate and contain the attack, whether malicious software, an exploited vulnerability, or stolen network account?
- Remediation: What tools and procedures will your response team follow to completely eradicate the attack, including locating the means of ingress to prevent future occurrences?
- What tools and procedures will your response team follow to completely eradicate the attack, including locating the means of ingress to prevent future occurrences?
- Recovery: What is the process for returning to a normal business state so that you can continue serving your member base.
- This is only possible with a solid business continuity program that includes protected, immutable data backups and available resources to recreate the production environment.
- Post-Incident Analysis: What did we learn about this incident and what steps can we take to strengthen our posture and enhance our response?
- What did you learn about this incident and what steps can you take to strengthen our posture and enhance our response?
- Risk Mitigation: Everything that is learned through each stage of the response as well as case studies from incidents reported by other financial institutions collectively teach us how to better mitigate and manage risk.
- This information must be disseminated to the response team and all staff through awareness and training events such as a simulation-based tabletop exercise.
All of the above should be documented in your Incident Response Plan and tested and reviewed regularly to ensure it remains relevant to credit union operations.
Resources available for CUSOs and Credit Unions
CU*Answers and AdvantageCIO have several services and resources to help you achieve your goals in this area.
Resources available to enhance the security posture for CUSOs and credit unions.
Due diligence documentation including risk assessment tools for:
- SecuriKey documentation for:
- It’s Me 247 online/mobile banking,
- MOP – membership opening process,
- MACO – multi-authentication convenience options, and
- idocVAULT – core image processing.
- Cybersecurity literacy video for credit union directors.
- Uptime tracking for CU*BASE core processing.
- To request a copy of the CU*Answers Business Continuity Plan (including Incident Response).
- Reports from recent recovery and high-availability rollover exercises.
- Services available to assist credit unions in preparing for an Incident Response.
- Services available to assist credit unions in preparing for IT audits and examinations.
- Click here to submit your question about Business Continuity or Incident Response.






![[The Pulse] HA Rollover Results Now Available](https://www.cuanswers.com/wp-content/uploads/The-Pulse-Disaster-Recovery-email-banner-7.21-300x121.png)


















